Music Copyright Infringement Technology & Applications Overview
July 28, 2025
1. Music Copyright Infringement Introduction
Copyright infringement is the broader legal term that covers any unauthorized use of a musical work. While it includes large-scale piracy, it also extends to more everyday violations, such as a business playing music without a public performance license or a brand using a popular song in an online ad without permission.
Music copyright infringement specifically refers to the unlawful copying, distribution, or downloading of protected audio content through file-sharing platforms, unauthorized software, or mobile apps. These actions not only violate the rights of creators but also cause significant financial harm to the music industry and the wider creative economy.
Two decades ago, the Institute for Policy Innovation estimated that copyright infringement cost the U.S. economy $12.5 billion annually, resulted in the loss of 71,060 jobs in the recording industry, and reduced annual earnings by $2.7 billion across the sound recording and retail sectors. Today, with the rapid growth of digital and user-generated content (UGC) platforms, tracking copyright infringement has become even more complex, making it difficult to quantify the full extent of the economic impact. Given these challenges, the true scale of the issue today is likely far greater.
Originally limited to illegal physical copies such as cassette tapes or records, music piracy exploded in the 1990s with the introduction of MP3 files. The launch of Napster in 1999 marked a turning point, enabling global sharing of music files and causing a dramatic drop in record industry revenues. This prompted lawsuits from major labels and artists. The problem worsened with the advent of torrent sites, which allowed users to download entire albums quickly and easily.
While legal streaming platforms like Spotify and Apple Music later emerged to provide legitimate, affordable access to large music catalogs, helping to reduce some forms of copyright infringement—unauthorized consumption remains widespread. In the 2020s, enforcement efforts shifted from shutting down "pirate" websites to targeting software developers that enable stream-ripping from services like YouTube. In 2022 alone, monitoring firm Muso recorded over 17 billion visits to music piracy websites.
Despite efforts such as stricter copyright laws, lawsuits, and digital rights management (DRM) systems, copyright infringement continues to threaten fair compensation for artists and complicates royalty tracking. Sustained vigilance, better enforcement tools, and industry-wide innovation remain essential to protecting intellectual property and ensuring the long-term sustainability of the music business.
2. Types of Music Copyright Infringement
Music copyright infringement takes many forms, with the most common types including, but not limited to:
-
Unauthorized Reuploads: Posting copyrighted music on personal channels or social media accounts without permission from the copyright holder. This includes uploading entire albums or individual songs to platforms like YouTube, TikTok, often to gain views, followers, or ad revenue.
-
Copying and Distributing Physical Media: Reproducing music onto CDs, cassettes, or vinyl records and distributing them without authorization. While more widespread in the past, this still happens today.
-
File Sharing: Illegally sharing music through P2P platforms, file-sharing apps, or cloud drives, allowing others to access and download copyrighted material.
-
Illegal Downloads: Obtaining music files from torrent sites or peer-to-peer (P2P) networks without purchasing them or receiving approval from the copyright owner.
-
Ripping Music: Extracting audio from physical media or digital services (like CDs or streaming platforms) and distributing the ripped files without authorization.
-
Illegal Streaming: Listening to music via unauthorized streaming sites or using hacked versions of legitimate services to avoid paying subscription fees.
-
Bootleg Recordings: Recording and distributing unauthorized versions of live performances, often without the artist’s knowledge or approval, and typically of poor quality.
-
Unauthorized Public Performance: Playing copyrighted music in commercial establishments (e.g., coffee shops, stores, bars) without required public performance licenses.
-
Unlicensed Background Music (UGC): Using copyrighted songs in user-generated content (videos, podcasts) on platforms like YouTube or TikTok without proper licenses.
3. Current Music Copyright Infringement Solutions
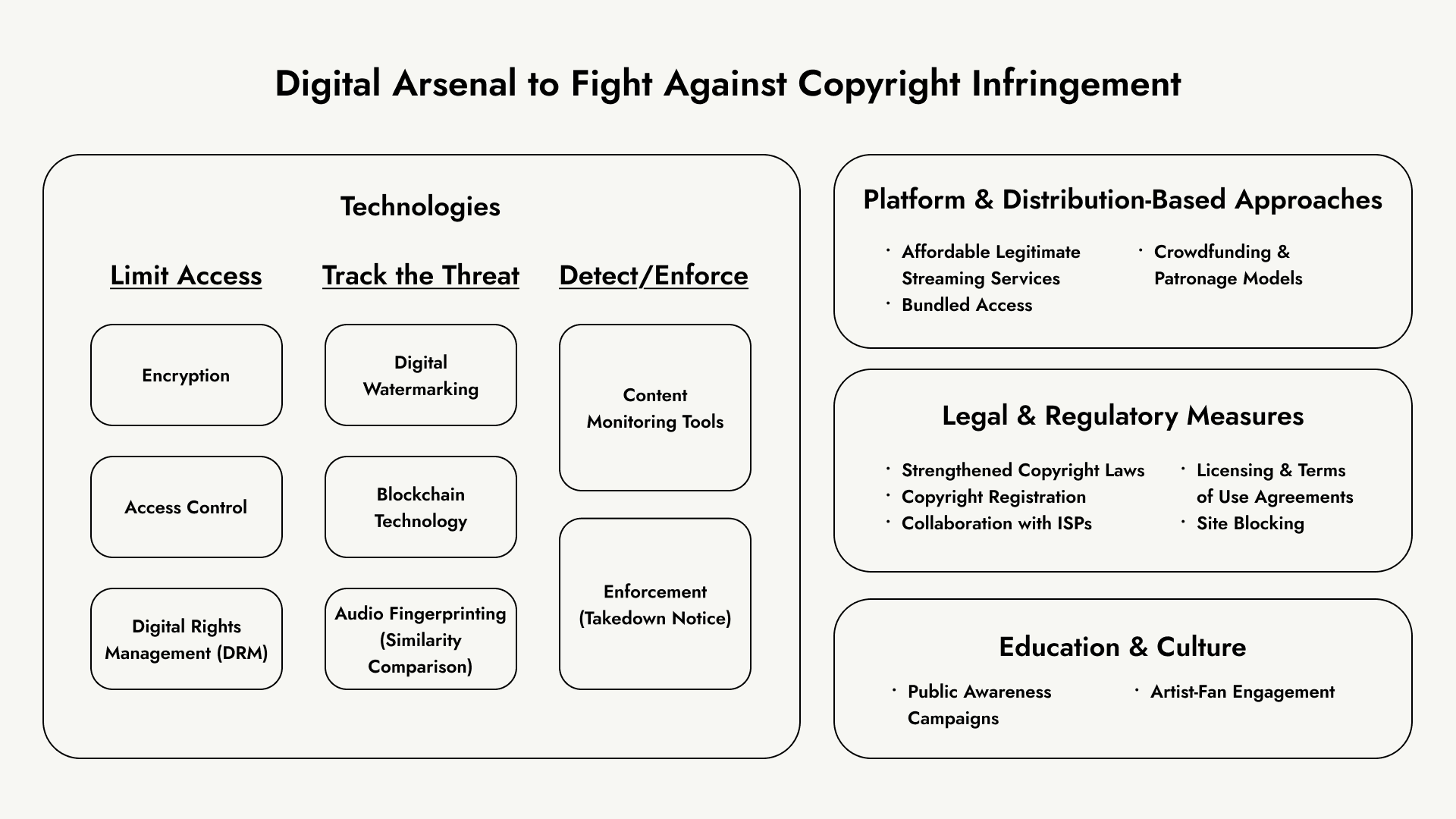
Efforts to combat music copyright infringement combine technological, legal, platform-based, and educational strategies. These approaches work across different stages of content creation, distribution, and consumption.
a. Content Protection Technology
- Types
1.1 Access & Protection (Pre-Piracy Prevention)
-
(1) Digital Rights Management (DRM): Controls how music files are accessed, copied, and played.
Example: DRM systems are used to control how music is accessed, copied, or shared. For example, when Apple first launched its iTunes Store, all purchased songs came with DRM restrictions. A college student who bought an album on iTunes discovered he couldn’t transfer the songs to his Android phone or burn them freely to CDs. While DRM protected rights holders from unauthorized distribution, it also frustrated users who felt restricted despite legally purchasing the music. These types of issues eventually led Apple to shift toward offering DRM-free music.
-
(2) Encryption: Secures content during transmission and storage to prevent unauthorized access or tampering.
Example: Encryption protects music during streaming or storage by scrambling data so it can’t be read without the proper decryption key. Spotify, for example, encrypts all streaming traffic between its servers and user devices. When a group of hackers attempted to intercept and download music files directly from Spotify’s data stream, they found only meaningless encrypted code. This ensured that even if the stream was captured, it couldn’t be used without breaking the encryption.
-
(3) Access Control: Limits who can view, download, or share content—often enforced via login credentials, subscriptions, or IP restrictions.
Example: Access control restricts who can listen to music based on factors like login status, subscription level, or location. A documentary about a famous jazz musician was available exclusively to U.S. Netflix subscribers. A jazz fan in Brazil, eager to watch, tried to access it but was blocked by the platform’s IP-based restrictions. He used a VPN to bypass the regional lock, technically violating the licensing terms, which shows both the strength and limitations of access control systems.
1.2 Tracking & Detection (Piracy Identification and Source Tracing)
-
(1) Watermarking: Embeds hidden identifiers in audio files to trace the origin of leaks without affecting listening quality.
Example: Watermarking embeds hidden, traceable codes into audio files without altering the listening experience. A major record label once distributed advance copies of a pop album to journalists ahead of its release, each embedded with a unique watermark. Days before the official drop, the album was leaked online. Using watermark detection, the label traced the leak back to a specific reviewer and revoked their early-access privileges, effectively preventing future leaks from that source.
-
(2) Audio Fingerprinting: Generates a unique digital signature to recognize music by analyzing key characteristics like tempo, pitch, and frequency patterns. It allows detection even if the music is slightly altered (e.g., trimmed, remixed, or pitch-shifted).
Examples:
- Content ID (YouTube): Matches uploaded videos to a database of copyrighted works and automatically monetizes, blocks, or tracks them.
- Audible Magic: Detects copyrighted music in real-time during livestreams or uploads for platforms like Twitch.
Example: Audio fingerprinting is used to detect music based on similarity comparison. For instance, a Twitch streamer played a remixed version of a well-known song during a live broadcast. Although the track had been sped up and layered with sound effects, the audio fingerprint is still very similar and the audio fingerprinting system will recognize it. As a result, the stream was flagged and partially muted for copyright infringement, demonstrating how powerful and precise this technology can be.
1.3 Monitoring & Enforcement (Post-Piracy Response)
-
Content Monitoring Tools: broader systems or services used to continuously watch for piracy, take action when it’s detected, and manage enforcement processes, includes:
- Crawlers & Web Scanners: Scan piracy sites, torrents, and forums.
- Takedown Systems: Automate or assist in sending DMCA notices or platform-based takedowns.
- Analytics Dashboards: Help rightsholders track where and how their content is being used.
Example: These tools include web crawlers, automated takedown systems, and dashboards that monitor and enforce copyright online. When a Korean entertainment company released a new single, it quickly appeared on file-sharing forums and torrent sites. Scanning tools enabled the label to identify unauthorized uploads within hours of the release. Takedown notices were immediately issued to infringing platforms, while the analytics dashboard revealed regional piracy trends, guiding targeted legal action.
1.4 Ownership, Transparency & Monetization
-
Blockchain Technology: Provides transparent, immutable records for ownership rights, licensing, and royalty payments across the content lifecycle.
Example: Blockchain offers a transparent, immutable way to track ownership and royalty distribution. On the music platform Audius, an independent artist uploaded her latest single. Every time a fan streamed or tipped her, the blockchain recorded the transaction in real time. This gave the artist immediate visibility into who was listening and how much she was earning—without relying on intermediaries or waiting for quarterly reports. It ensured her work was securely tracked and fairly monetized.
- Comparison
| Technology | Function | Timing | Pros | Cons |
|---|---|---|---|---|
| Encryption | Protects files during download, streaming, or storage. | Pre-access | Prevents interception and tampering; protects data integrity. | Does not stop access once decrypted; complex implementation. |
| Watermarking | Traces pirated content to its source. | Pre-release | Survives file conversion; discreetly identifies leak sources. | Does not prevent piracy; may influence audio quality; requires special tools for detection. |
| Access Controls | Limits who can use or share content (e.g., subscriptions, logins). | At point of access | Effective for region, user, or subscription-based control. | Can be bypassed (e.g., with VPNs); not foolproof. |
| DRM | Restricts copying, playback, and distribution. | At distribution / playback | Enforces licensing; limits unauthorized distribution. | Can frustrate users; may be bypassed; costly to implement. |
| Content ID / Fingerprinting | Scans for unauthorized use in uploads/streams. | Real-time / Post-upload | Highly accurate; detects altered/remixed audio. | Resource-intensive; may fail with heavily modified content. |
| Content Monitoring Tools | Detect and respond to piracy via fingerprinting, scanning, and takedown systems. | Continuous / post-piracy | Scalable enforcement; tracks trends and issues takedowns. | Dependent on detection accuracy; legal action still needed. |
| Blockchain | Tracks ownership, usage, and royalties transparently. | Throughout lifecycle | Transparent and tamper-proof; ensures fair compensation. | Adoption challenges; not yet industry standard. |
b. Platform and Distribution-Based Approaches
-
Affordable Legal Streaming Services: Platforms like Spotify and Apple Music reduce the appeal of piracy by offering accessible legal alternatives.
-
Bundled Access: Integration of music access with hardware purchases or service subscriptions (e.g., phones with free streaming plans).
-
Crowdfunding & Patronage Models: Direct support for artists through platforms like Patreon creates new, legal revenue streams outside traditional distribution.
c. Legal and Regulatory Measures
-
Strengthened Copyright Laws: Modernized legislation improves protections for digital content and streamlines enforcement against infringement.
-
Copyright Registration: Official registration of works simplifies ownership verification and supports legal action against piracy.
-
Licensing & Terms of Use Agreements: Clear usage terms help define how content may legally be accessed and shared.
-
Collaboration with ISPs: Internet service providers assist in issuing warnings to violators, throttling traffic, or suspending accounts.
-
Site Blocking: Governments and rightsholders work to block access to known piracy websites.
d. Education and Culture Shift
-
Public Awareness Campaigns: Educational efforts inform users about the ethical and legal consequences of piracy.
-
Artist-Fan Engagement: Direct marketing and content sharing strengthen the fan community and encourage legal support for creators.
4. Structural Limitations in Today’s Digital Rights Technologies
While the digital rights ecosystem has evolved into a sophisticated network of tools and services, the fundamental technologies that underpin these solutions share critical limitations. Whether delivered through specialized providers or integrated platforms, most offerings today rely on a common set of techniques—such as digital rights management (DRM), fingerprinting, watermarking, and content ID systems—that are increasingly showing their age.
Despite their broad adoption, these approaches face three systemic disadvantages:
- Bypassability: Access-control methods like DRM and file-based watermarking can be circumvented by skilled users. Whether through decryption, re-encoding, or simply re-recording the content externally (the "analog hole"), these protections are often rendered ineffective.
- Inefficiency: Many detection systems, particularly those using fingerprinting, rely on comparing content against massive reference databases. This process is computationally intensive and frequently dependent on human intervention, resulting in substantial delays—during which piracy can spread—and high operational costs.
- Fragility: Current solutions are fragile in the face of modern content manipulation. Simple edits, remixes, or audio degradation can cause fingerprinting systems to fail, meaning that slight alterations are enough to evade detection entirely.
These limitations are not isolated to individual products—they are structural weaknesses shared across the entire landscape of content protection technologies. Even the most streamlined all-in-one platforms remain constrained by these inherited flaws.
5. Next-Generation Watermarking: OfSpectrum Inaudible Watermark
In response to the structural limitations that persist across current digital rights enforcement technologies, OfSpectrum introduces a fundamentally different technical approach: inaudible watermarking. Rather than repackaging existing methods, this solution redefines how content is protected, detected, and monetized at the audio level.
Developed using neural networks and grounded in psychoacoustic theory, OfSpectrum’s watermark is embedded directly into the audio waveform and is imperceptible to human ears. By becoming part of the sound’s physical structure, the watermark is inherently more robust against common forms of manipulation, including remixing, editing, and analog re-recording.
Unlike fingerprinting-based systems that rely on matching content to massive reference databases, OfSpectrum’s detection process simply identifies the presence of the watermark within the wave. This architecture significantly reduces processing time and resource consumption. Benchmarks indicate that this method can operate over 100x faster than traditional fingerprinting, allowing for near real-time detection of infringing content.
In addition to speed and robustness, the system is highly scalable. As fingerprinting systems scale poorly with longer content—requiring exponentially more resources—OfSpectrum’s detection scales linearly, making it accessible for smaller rights holders and independent creators without compromising performance.
A further point of differentiation lies in the integration of monetization tools directly within the watermark. The system supports the embedding of licensing metadata, purchase links, and premium access triggers, enabling redirection of audiences from pirated content back to authorized channels. This not only supports enforcement but also introduces new pathways for revenue recovery and legitimate distribution.
In summary, OfSpectrum offers an end-to-end watermarking infrastructure that combines:
- Inaudible audio watermarking
- Robust and efficient real-time detection
- Automated enforcement workflows
- Embedded monetization and licensing capabilities
By addressing long-standing inefficiencies in both cost and performance, this approach makes robust digital rights protection technically viable and economically accessible for a wider segment of the creative economy. It represents a scalable and forward-looking alternative to traditional methods—and a potential new standard for the future of content protection.
Conclusion
As the digital music landscape continues to evolve, so too do the challenges of protecting intellectual property in a rapidly expanding and decentralized ecosystem. From unauthorized streaming and downloads to misuse on social platforms, music copyright infringement remains a persistent threat to artists, labels, and rights holders worldwide.
This report outlines the various forms of infringement, surveyed the range of current solutions, and analyzed the key players in the market. While many existing technologies provide essential tools for detection, enforcement, and rights management, gaps remain, particularly in areas like robustness, real-time response, cross-platform consistency, and revenue recovery from infringing use.
To address these shortcomings, next-generation solutions like OfSpectrum Inaudible Watermark are emerging to unify watermarking, automated enforcement, and monetization in a single, scalable platform.
The future of music copyright protection will depend on such innovation, where precision, speed, and commercial impact converge to uphold the value of creative work in the digital era.
